In today's ever-changing digital landscape, institutional investors face the daunting task of safeguarding their data from cyber threats, especially those that exploit the power of artificial intelligence. To shed light on this pressing issue, Vidrio Financial presents valuable insights and a forward-looking perspective for allocators.
By: David Barry, Director of Marketing, Vidrio Financial
As institutional investor portfolios become increasingly intricate and investment teams become more adept at analyzing strategies that yield alpha, it is unfortunate that cyberattacks and the associated cyber risks faced by investors are also growing.
In March of last year, McKinsey & Company published an enlightening article that delved into the correlation between cyber threats and organizational cyber expenditures. You can access the comprehensive article here, along with the accompanying visual analysis below:
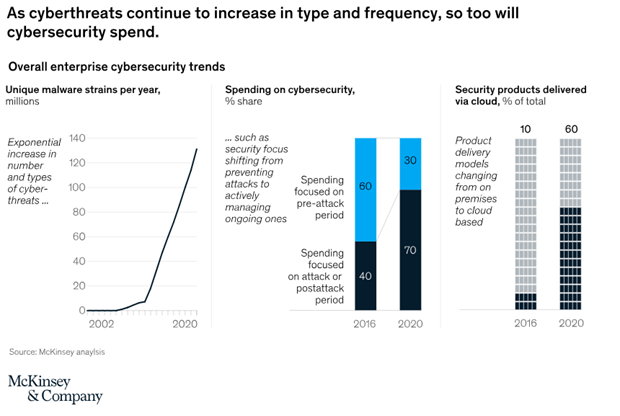
Types of attacks institutional investors should be aware of:
Investors face a multitude of cyber threats, with the number of attacks steadily increasing. Among the most prevalent are:
Ransomware: a type of malware that permanently blocks access to the victim's personal data unless a ransom is paid.
Phishing: a fraudulent practice of sending emails or other messages purporting to be from reputable companies to induce individuals to reveal personal information like passwords, social security information, and/or credit card numbers.
Data Breach: the release of confidential, private, or otherwise sensitive information into an unsecured environment. In this context, it occurs because of a deliberate attack.
DOS and DDOS attack: an attack that is designed to overwhelm system resources. Once the system falls prey to this attack, any request is blocked and denied fulfillment.
Recently, the New York Department of Financial Services rolled out some updated standards as it relates to cybersecurity from banks, insurers, and even software solutions, like Vidrio Financial. Adrienne Harris, New York State Superintendent of Financial Services was quoted as stating, “Cyberattacks are on the rise, and the updates require the financial services industry to institute stronger standards and controls to secure sensitive data,” Adrienne went on to explain that, “Expanded use of proven protections such as multi-factor authentication will be required while maintaining the risk-based flexibility of the landmark cybersecurity regulations.” You can read more about the updated rules here. Given this backdrop, we believe this might be a good opportunity to review how Vidrio looks at cybersecurity and how we see this theme expanding in the future.
To set the stage, it’s helpful to understand Vidrio’s position in the institutional market. Vidrio’s platform combines premier software and exceptional human expertise for institutional investors managing portfolios of direct investment and allocations to external managers across traditional and alternative asset classes. As software and human interactions continue to overlap within the industry, it will become increasingly important for investors to rely on a secure solution that covers the full investment life cycle across data collection, manager research and monitoring, investment valuation and reconciliation, risk analytics, and advanced level reporting. This is where Vidrio’s platform truly shines. That entire investment life cycle needs to be relied upon as a source of historical data truth, secured from any outside threat, and can be acted upon to adjust asset allocations according to market moves.
Vidrio’s view on cybersecurity
As we look ahead, we remain fully committed to continuing to support industry leading protections and believe investors need to remain vigilant in closely monitoring the ever-changing cyber landscape. This is not only a priority for our current clients, but also for those who are planning to join our platform in the near future. At Vidrio, we hold security in the highest regard and uphold industry-leading standards within a framework that can be easily categorized into the following:
1. Test, strategize, and plan.
2. Run vulnerability assessments and penetration tests.
3. Scale integration and deployment.
4. Understand industry standards and baselines.
5. Enhance intelligence, monitoring, and training.
We believe that having a well-defined testing strategy and plan is essential for any allocation team to establish a solid foundation that aligns with an organization's security objectives. These objectives may include critical systems for business operations, approved third-party applications, or the most valuable strategic asset - your data. Once you have carefully crafted your cyber-assessment strategy, it is important for your organization to understand the types of tests that need to be conducted, establish a minimum frequency to mitigate higher risks, and determine the responsibility within the organization to maintain those tests.
Over the years, Vidrio has expanded its own testing capabilities to both automated and manual approaches. In terms of automation, the AI evolution is still early but has also already brought changes to cybersecurity methodology in the form of natural language processing, facial recognition, and addressing threat alerts.
While automation can make lives easier in forecasting new attacks, it can also make those attacks more complex as smarter malware can evade various threat alerts that an investment organization may have in place. If your business isn’t innovating and reviewing their threat assessments on a regular basis, then that could leave investor data open for hacks.
To further drive the point home of having the right starting point for cybersecurity, we wanted to give a shoutout to Konbriefing.com on one of the best 2023 cybersecurity maps that highlights this growing global threat – you can see more of this research here.
Moreover, we believe vulnerability and penetration testing can play a crucial role in assisting institutional investors in addressing security weaknesses. By conducting active scanning and testing exercises that simulate real-world attacks, organizations can also uncover exploitable vulnerabilities that may go unnoticed by automated security processes. Vidrio believes it is imperative for institutional investor organizations to incorporate testing tools into their future operational innovations and overall business growth. Furthermore, these tools should be aligned with industry best practices and regulatory requirements for maximum effectiveness.
In order to create a comprehensive cybersecurity process, the final piece seamlessly incorporates monitoring, training, review, and improvement cycles.
As the threat landscape continues to evolve and become more sophisticated, we believe it is imperative to have stronger monitoring capabilities and incident reporting mechanisms. Training and education can play a crucial role in empowering institutional investment teams to operate at the highest level, keeping them informed about emerging security trends and best practices, ultimately minimizing the risk of security vulnerabilities. Once training and education are fully integrated into the organization, regular reviews can be scheduled, and strategies for improvement can be implemented as the organization grows. In the category of emerging security trends, it was only last month that a security fix was issued against the Citrix Bleed flaw, following abuse by hackers spanning several weeks. As you can imagine, patches were rolled out, but adoption took time, leaving hackers to accelerate their attacks while organizations scrambled to fix the vulnerability.
In addition to these guiding principles above, we have observed a significant increase in the adoption of multi-factor authentication practices, single-sign-on access, and policies rooted in a zero-trust philosophy. This philosophy is predicated on the fact that attackers can exist both inside and outside a given network, which is why no user or machine should be automatically trusted. Instead, users must verify their identity, privileges, and device security to ensure maximum protection for the benefit of their organizations. Devices are especially important as work mobility continues to rise. Handheld devices can also be a huge attraction to potential hackers, given the need to “always be on” and connected to work discussions. Therefore, incorporating this guidance on both in-house and remote/mobile devices will help reduce vulnerable points of access in the future.






